What are Slack Audit Logs?
Like many Software program as a Service (SaaS) choices, Slack gives audit logs to Enterprise Grid clients that document when entities take an motion on the platform. For instance, when a person logs in, when a person updates their profile, when an app downloads a file, and so on. The precise list of actions which might be captured within the audit logs is kind of in depth and it’s value perusing periodically for any new additions. The documentation additionally presents an example audit log and discusses the fields intimately. We recommend reviewing this documentation earlier than continuing additional, and we’ve included an aesthetically pleasing instance audit log that you should utilize to check your newfound audit log experience:
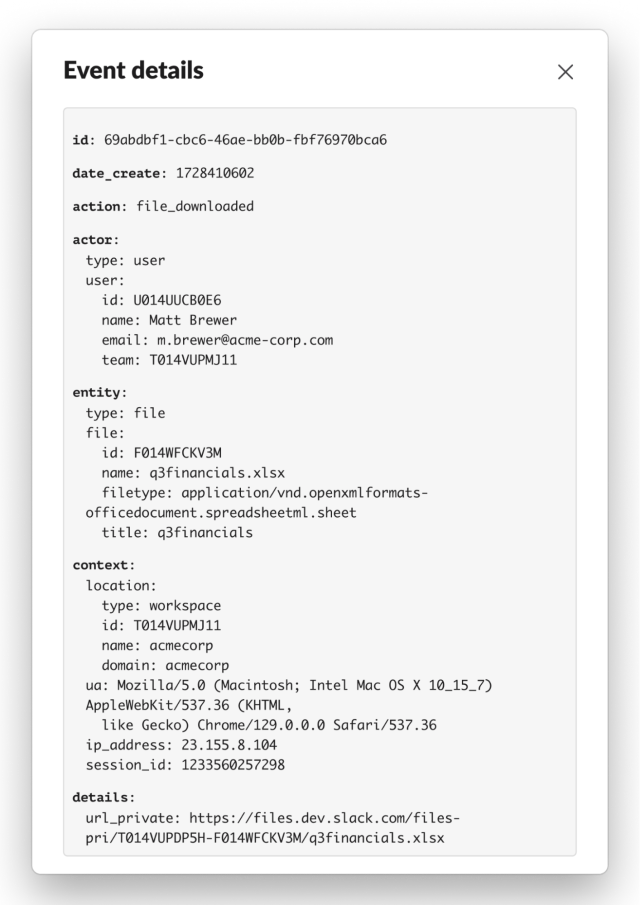
The place are Slack Audit Logs Out there?
Slack audit logs can be found to Org Admins, House owners, and people with the Audit Logs Admin role through the Audit Log Dashboard by clicking Instruments and Settings → Handle Audit Logs . We are going to go over a extra detailed instance of utilizing the UI to work together with audit logs in a subsequent part. The audit logs are additionally out there through an API, and plenty of distributors have connectors out there to ingest the audit logs into their platforms. Just a few examples embody:
The Audit Log API permits for filtering by attributes like when the logs had been generated, the motion (as much as 30 actions could also be specified), actor, and entity. For instance, if an enterprise was solely concerned about consuming the person login occasions from the audit logs, they may specify user_login for the motion parameter when calling the API. Please see the API documentation for extra element.
Anomaly Occasions
What are Anomalies?
Included within the stream of audit logs are anomaly occasions (occasions with an motion of anomaly). These differ from different audit logs occasions as a result of, as an alternative of recording an motion that an entity carried out on the platform, they point out that Slack’s evaluation pipelines have detected an entity performing an anomalous motion (or set of actions) or the circumstances beneath which an entity carried out an motion are anomalous. Anomalies function indicators of bizarre or probably suspicious exercise inside your Slack workspace. For a complete checklist of at present deployed anomalies and steering on the way to interpret them, please confer with our documentation. We strongly advocate reviewing this useful resource to realize a deeper understanding of obtainable anomalies earlier than continuing additional.
The right way to use Anomalies?
As with all new occasion supply that a company onboards, Slack anomalies require some investigation, experimentation, and evaluation earlier than they are often operationalized by a Detection and Response group.
Generally, anomalies aren’t one thing that a company would wish to instantly increase as an incident. They point out that one thing sudden occurred and additional investigation could also be warranted. The significance of an anomaly varies relying on every group’s insurance policies and permitted actions. As an illustration, if a user_agent anomaly is detected with a brand new Person Agent like Go-http-client/2.0, it’d point out somebody is utilizing an automatic device to work together with Slack, quite than accessing it by means of the Slack app or web site. For some organizations, utilizing unsanctioned Slack purchasers might not be allowed by coverage, so the safety group would wish to comply with up with this person. Different organizations might enable their customers extra latitude, so this anomaly can be much less fascinating to them.
Allowlisting CIDR Ranges and ASNs
If a company is aware of that sure IP addresses or community ranges are related to official actions, Slack gives a method for patrons to allowlist these sources. These API endpoints enable one so as to add trusted CIDR ranges and ASNs, offering versatile choices to fine-tune anomaly detection and cut back anomaly quantity.
Correlating Anomalies
Correlating a number of anomalies can present precious insights into potential safety issues. As an illustration, think about a situation the place a user_agent anomaly happens close to an excessive_downloads anomaly. This mix may counsel a scraping device is getting used (word there’s additionally a newly launched, excessive constancy unexpected_scraping anomaly for sure scraping eventualities). The importance of this exercise will rely in your group’s insurance policies. Nonetheless, the scenario turns into extra vital if an ip_address or session_fingerprint anomaly accompanies the beforehand talked about anomalies. This mix may point out that an exterior celebration has obtained a person’s cookie and is utilizing it to scrape information. In such instances, most organizations would doubtless prioritize a radical investigation.
Aggregating Anomalies
Lastly, we are able to mixture some anomalies to floor eventualities we’re concerned about. For instance, a company may observe a number of customers producing excessive_downloads anomalies every day, however the anomalies might not characterize malicious exercise (benign outliers). Inspecting what number of excessive_downloads anomalies a person generated over some time period and evaluating the entire to historic norms may assist uncover conditions the place a person is performing undesirable exercise like scraping giant quantities of knowledge. For instance, if a company has by no means seen one among their customers generate greater than three excessive_downloads occasions in a day, they may search for instances the place 4 or extra excessive_downloads anomalies happen for a person and examine these extra carefully.
Context from Audit Log Occasions
Anomaly logs have considerably decrease quantity than audit logs, sometimes by a minimum of two orders of magnitude, so if a company is concerned about remaining conscious of anomaly logs however can not deal with the total quantity of their audit logs, they’ll filter for simply anomalies utilizing the strategy outlined earlier. That stated, we extremely advocate consuming the whole lot of your audit logs at any time when attainable so you’ve gotten essentially the most quantity of surrounding context attainable when investigating anomaly logs. For instance, the encompassing file_downloaded audit logs occasions present extra context when a person triggers an excessive_downloads anomaly, permitting you to substantiate which recordsdata had been really downloaded. Moreover, in an Incident Response situation, having the audit logs out there regionally in a simply queryable type can save time and stress.
Audit Log UI Instance
If you need to assessment your Slack audit logs with out an exterior service, Slack gives a UI that may be reached from Instruments and Settings → Handle Audit Logs. To exhibit the way to use the UI, we are able to stroll by means of some exercise from a salesman, Matt, who’s leaving the fictional firm, Acme Corp. First we’ll load the principle Audit logs tab:
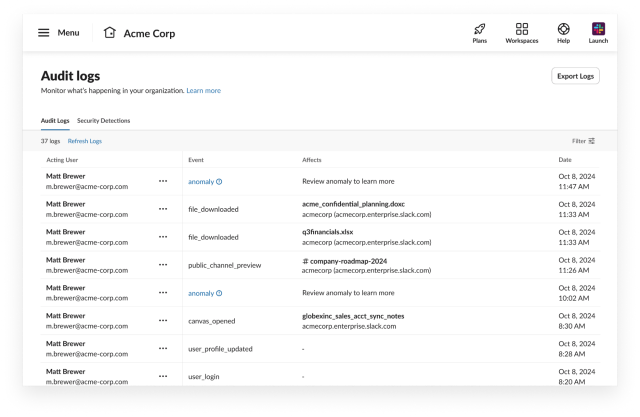
Then, we’ll swap to the Safety Detections tab to see any anomalies that Matt has generated:
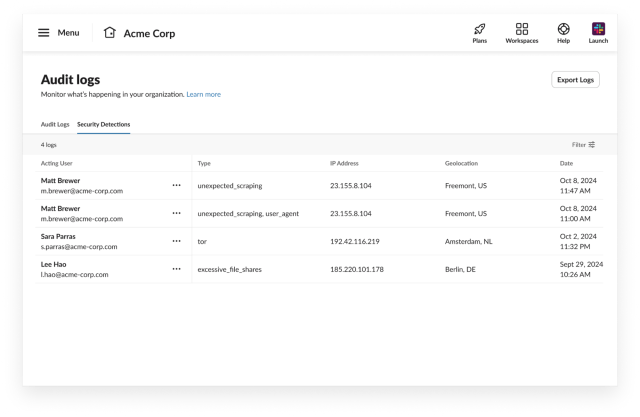
We see that Matt generated a number of anomalies. By clicking on the ••• menu after which View Full Log Particulars, we are able to discover out extra details about an anomaly. The primary one is a twofer and has the explanations unexpected_scraping and user_agent. The previous signifies that scraping was detected from Matt, and the latter signifies that Matt’s person agent modified – on this case to Scrapers Inc. Scrapers Inc will not be a person agent related to any sanctioned Slack consumer and subsequently we’d not count on person exercise from it. Observe: if an unexpected_scraping anomaly appeared by itself, the Person Agent would nonetheless be included, so strictly talking we didn’t want the user_agent anomaly to find out that Matt is utilizing an sudden consumer.
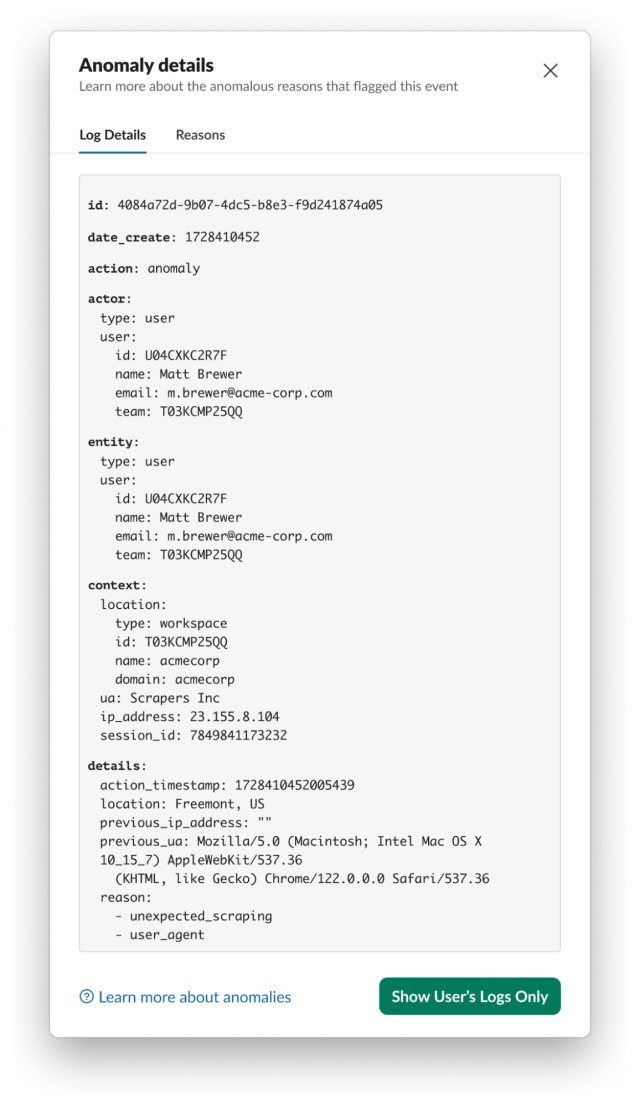
The opposite anomaly that Matt generated is excessive_downloads, and it’s additional proof that Matt is scraping information from the Slack workspace. Once more, we are able to see that the exercise is coming from a consumer with person agent Scrapers Inc.
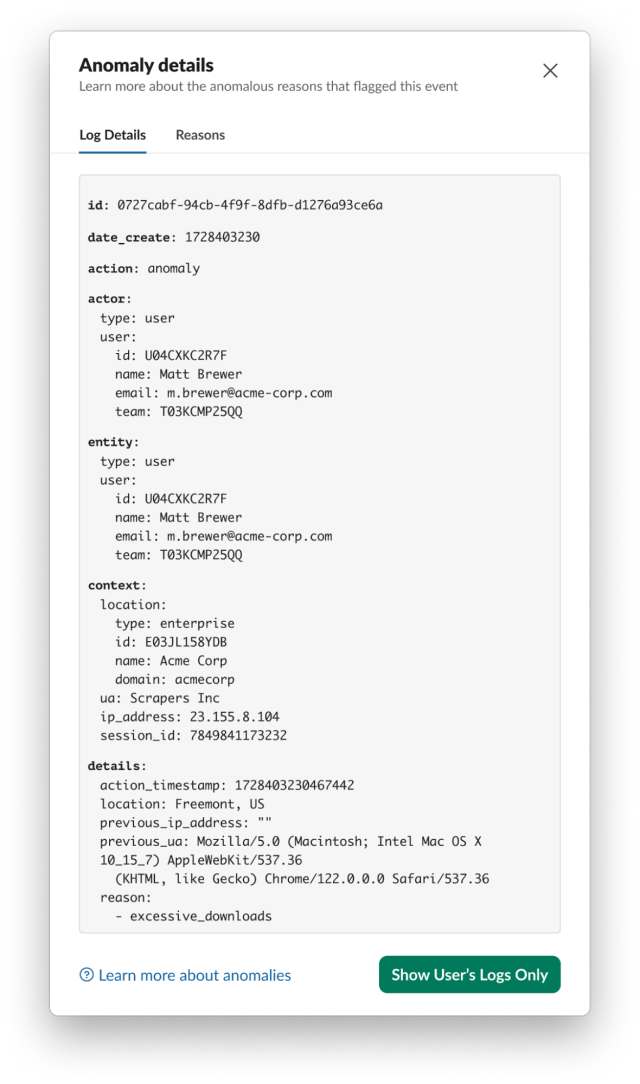
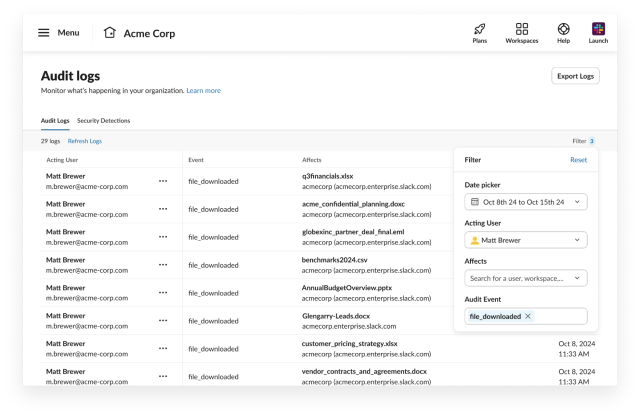
Since Matt is leaving the corporate, we wish to know what kind of recordsdata he’s downloading, so we flip again to the Audit Logs tab and filter for file_downloaded occasions:
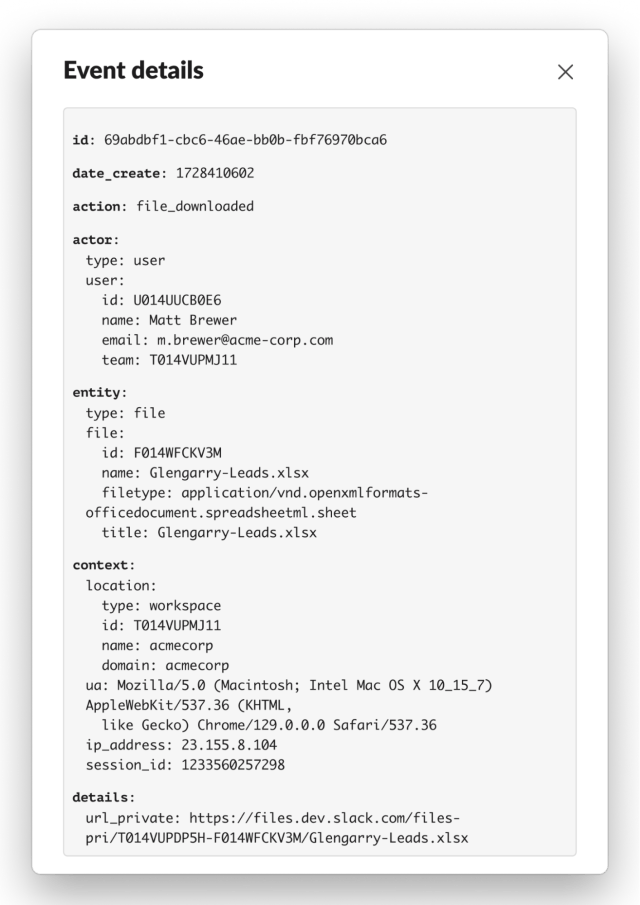
Then, we look at one of many recordsdata by clicking the ••• menu after which View Full Log Particulars. The file is known as Glengarry-Leads.xlsx which might be not one thing Acme Corp would need a salesperson to be retrieving as they depart.
Terminating a Person’s Energetic Classes
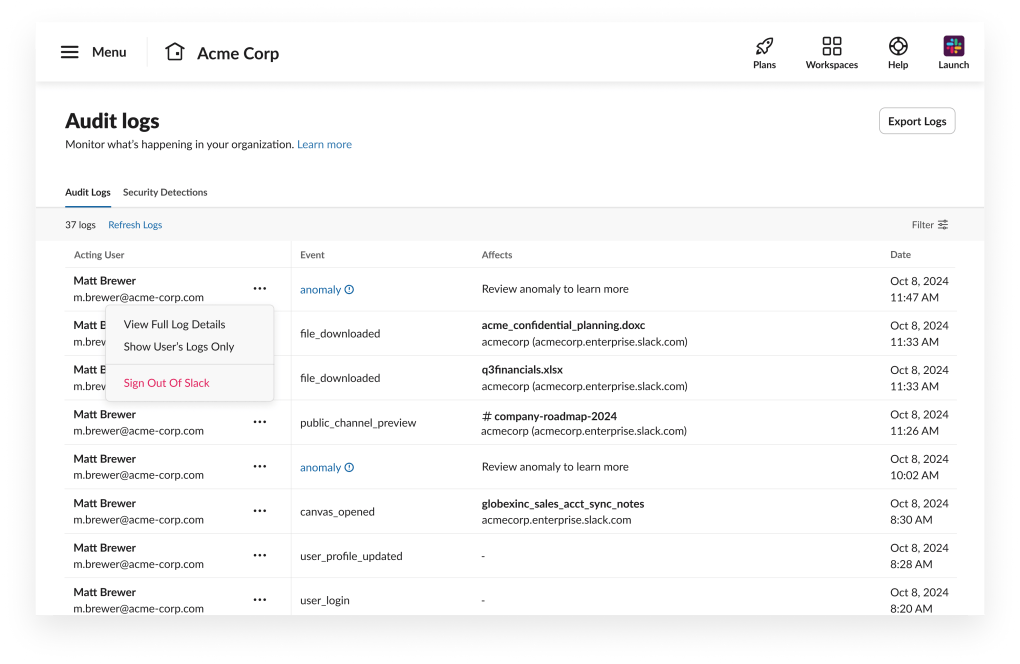
In the event you determine suspicious exercise related to a person’s account and wish to take instant motion, it’s attainable to terminate a person’s lively periods instantly from the Audit Logs dashboard. To do that, navigate to the precise anomaly log entry belonging to the person in query, click on the ••• menu, and choose Signal Out Of Slack. This motion instantly invalidates all lively periods for the person, forcing them to re-authenticate earlier than regaining entry to their account on any of their gadgets. (Alternatively, you’ll be able to selectively terminate the person’s lively periods by system sort, akin to cell or desktop solely, for those who require extra granular management over how and the place the person is impacted).
Different Detection Ideas
An ip_address anomaly was not generated for Matt’s exercise on this scenario, however, if it had been, an analyst would wish to decide if the triggering IP is one which they might count on Matt to be accessing Slack from (has he used it traditionally when accessing firm techniques, is it a VPN endpoint, is it recognized to be malicious, and so on.). If the IP will not be one which Matt is predicted to make use of, then this exercise may point out {that a} malicious actor has obtained entry to Matt’s account and is scraping information. Generally, we advocate checking the IP handle included in anomalies beneath investigation no matter whether or not an ip_address anomaly was generated for the person.
Equally, if a session_fingerprint anomaly had been generated for Matt across the time of those anomalies, it’d point out that Matt’s session cookie was exfiltrated and is being utilized by a malicious actor to scrape information. Once more, we advocate investigating the IP handle contained within the anomaly, and utilizing different sources of telemetry like logs from brokers operating on Matt’s endpoint to make sure that he’s accountable for the exercise.
As we mentioned earlier, the person agent related to anomalies like excessive_downloads, user_agent and ip_address generally is a good sign that scraping or different undesirable exercise is happening. We are able to operationalize this perception by surfacing anomalies with an sudden person agent. Moderately than making an attempt to enumerate all attainable sudden person brokers, it’s a lot simpler to search for instances the place the person agent will not be in a set of anticipated values for a company (assume allowlist vs blocklist).











