At Slack, we’re dedicated to safety that goes past the abnormal. We constantly try to earn and keep consumer belief by safeguarding important parts integral to each consumer’s expertise. From passwords to session cookies, and tokens to webhooks, we prioritize defending all the pieces important to how customers log into the platform and stay authenticated. By means of proactive measures and modern automations that leverage cutting-edge menace intelligence, we’re devoted to shielding customers from potential breaches, cookie hijacking malware, and inadvertent publicity of delicate info and secrets and techniques.
Secrets and techniques ought to stay secret
Slack’s technique has at all times been to anticipate and mitigate threats earlier than they’ll influence our customers. Since 20161, we’ve labored to proactively invalidate credentials uncovered on the web primarily based on common expressions2 tailor-made to the specifics of our tokens and webhooks. Oftentimes these secrets and techniques get inadvertently uncovered once they get hard-coded into growth code after which printed someplace like GitHub. Since these secrets and techniques present various ranges of entry to a consumer’s workspace, our tooling mechanically and instantly invalidates tokens and webhooks upon discovery and notifies their respective house owners.
Following this, we aimed to increase the identical degree of safety and automation to Slack passwords and session cookies. Password reuse throughout a number of platforms poses a big threat to consumer safety. A 2023 examine on account takeovers discovered that 70% of victims reported that they reused the identical password throughout a number of websites and companies, resulting in 53% of them having had a number of accounts taken over.3 Put in numbers, 29% of American adults skilled an account takeover by 2023, equating to roughly 77.5 million victims in response to authorities inhabitants figures.4 On the identical time, passwords and session cookies are additionally prone to malware that’s constructed to steal it from a consumer’s browser, one thing we’ll get into beneath.
Uncovered password detection and rotation
This led us to collaborate with strategic menace intelligence companions who acquire information from various sources similar to breaches, darkish net boards, botnets, and malware. These partnerships present us with high-fidelity, actionable information in real-time that lets us keep forward of menace actors, whereas additionally making Slack a much less interesting goal by rendering credentials stolen by these menace actors invalid and ineffective.
We constantly ingest this menace intelligence by way of our companions’ APIs and proactively discover matches between the credentials of our customers and people showing in menace actor datastreams. When a match is discovered, that credential is straight away reset and blocked from being reused by the related consumer sooner or later now that it’s compromised. Oftentimes we are able to catch these weak passwords so shortly that we’re in a position to reset them earlier than a menace actor is ready to use them to achieve unauthorized entry to an account.
This technique of evaluating passwords supplied by our menace intelligence companions with entries in our database isn’t easy, nonetheless. Whereas credential breach information is offered in plaintext, permitting unhealthy actors to make use of it, Slack passwords are securely saved as salted hashes, making a direct comparability unimaginable. To unravel this, we created a knowledge pipeline that mechanically ingests candidate credentials from our menace intelligence information sources after which salts and hashes every password so {that a} comparability to Slack’s database will be made earlier than the datapoint is purposefully—and completely—discarded.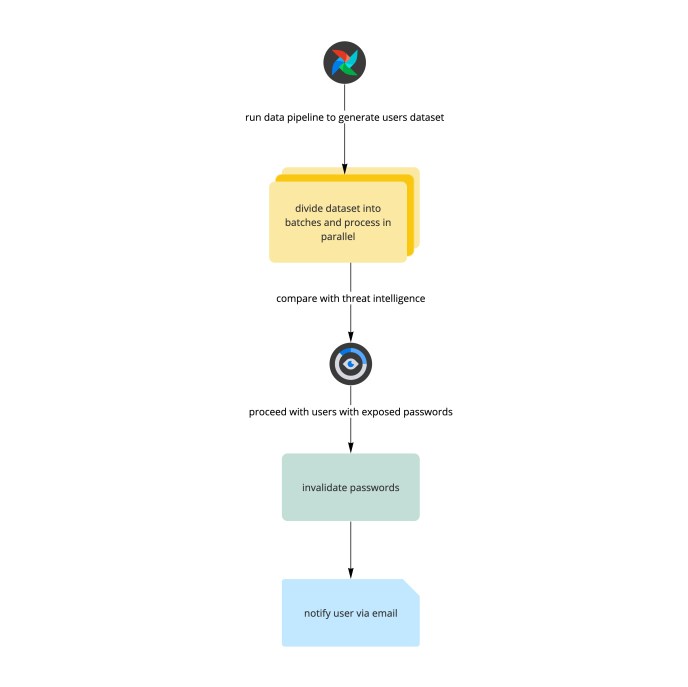
Though the method of salting and hashing every candidate password is intentionally time consuming, we’re in a position to course of thousands and thousands of credentials5 in an affordable period of time inside the safe confines of Slack’s backend. We accomplish this by dividing them into smaller batches and processing them in parallel in a job queue. When our backend course of identifies a match, the related consumer’s password is straight away reset and the consumer is notified by way of an e mail explaining this exercise, alongside some follow-up actions they’ll take to enhance the safety of their account going ahead. At this level or if no match is discovered, the pipeline discards the datapoint so menace intelligence information is rarely amassed or saved by Slack.
Invalidating hijacked cookies
All cookies of any app or service, together with the Slack session cookie every Slack consumer possesses, are domestically saved on a consumer’s machine. This native storage affords advantages like pace, effectivity, scalability, and offline performance, nevertheless it additionally produces a safety threat. If a menace actor is ready to compromise that consumer’s machine, they may additionally achieve entry to the cookies on that machine and use the Slack cookies to achieve entry to the consumer’s workspaces.
To proactively guard in opposition to this risk, aside from monitoring for signs of cookie misuse within Slack, we additionally always monitor menace intelligence datastreams and invalidate exfiltrated Slack cookies in a well timed method, balancing safety with consumer expertise. This extends the preliminary system we applied that discovers and invalidates consumer session tokens on a Slack consumer’s behalf so the cookies are additionally shielded from malicious use.
Oftentimes, our menace intelligence companions uncover hijacked Slack cookies so shortly6 that we’re in a position to not solely invalidate every earlier than a foul actor might have the possibility to misuse them, however in a approach that’s tailor-made to every respective consumer’s geography and timezone. When a Slack cookie is invalidated, its related session will get marked for termination, which as soon as full logs the consumer out of their workspace. That’s factor, by way of defending the consumer’s accounts from unauthorized entry, however we additionally know nobody needs to lose entry to Slack throughout a important dialog or in the midst of presenting in a huddle.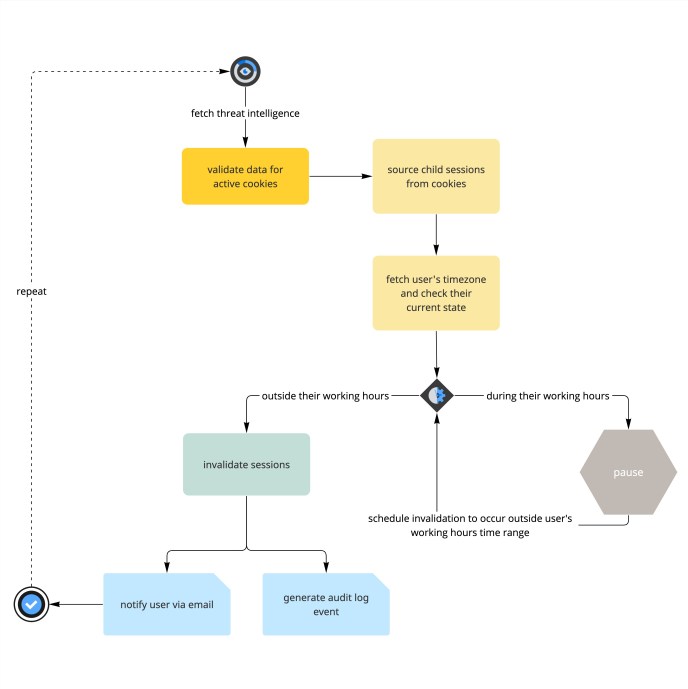
Throughout runtime, our automation evaluations every compromised cookie to judge whether or not the related consumer’s geography means it’s throughout their typical weekday working hours. In that case, the invalidation of that particular cookie is scheduled to happen in a time window exterior of that vary, whereas cookies belonging to customers who usually are not at the moment inside their weekday working hours are invalidated instantly. This lets us present a optimistic consumer expertise that considers every consumer’s timezone whereas calculating essentially the most environment friendly and well timed invalidation for the exfiltrated cookie.
As with uncovered passwords, when a cookie will get invalidated we notify the impacted consumer by way of e mail. Moreover, if that consumer’s workspace is on an Enterprise plan supporting Slack Audit Logs, we additionally add an occasion for the cookie invalidation into their audit logs for transparency.
Conclusion
Our dedication to safety at Slack extends past standard measures by leveraging leading edge menace intelligence with modern automations for locating and invalidating weak consumer credentials at scale. We firmly consider that proactively safeguarding in opposition to present and rising threats is just not solely a necessity for fostering a safe platform, however important for sustaining consumer belief in our model. We additionally pleasure ourselves on designing approaches that emphasize a seamless and clear consumer expertise, all whereas concurrently implementing strong safety protocols to thwart unauthorized entry makes an attempt by menace actors.
Fascinated with serving to us shield Slack customers? Apply now











